Algorithms
InfraMonitor is based on three main algorithms - AFD, IA, and BISL - summarized below. References for each algorithm are provided in each section.
See the repository.
1. The Adaptive F Detector
The Adaptive F-detector (AFD) technique is outlined by Arrowsmith et al. (2008, 2009). In contrast with other routinely used infrasound detectors, the AFD utilizes a contextual detection hypothesis that adaptively accounts for temporally variable correlated ambient noise. This technique reduces the number of false alarms caused by background noise sources such as ocean noise, wind farms, and other continuous wave sources.
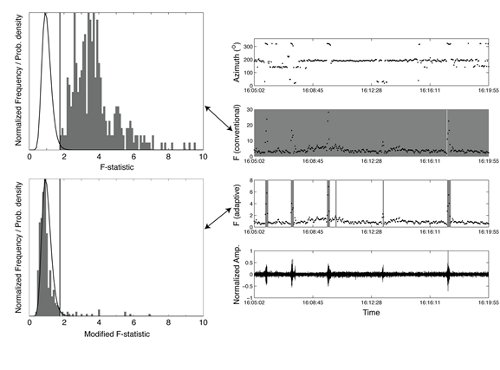
Figure illustrating the AFD method in comparison with a conventional F-detector for infrasound data containing five transient signals from mine shots but contaminated by wind farm noise. The conventional detector identifies the full data segment as a detection (represented by shaded gray areas on the right panel) whereas the AFD only detects the mining explosion signals.
2. Association
The infrasound association (IA) algorithm uses a grid search approach to relate arrivals at multiple arrays (Arrowsmith et al., 2008). InfraMonitor searches for groups of arrivals with backazimuths and inter-array delay times that are consistent with each grid node. When such groups of arrivals are identified, they are associated and input to the localization procedure described below.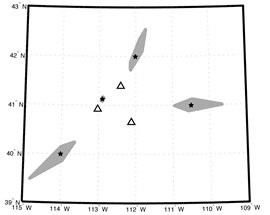
Association: Gray areas represent grid nodes associated with test events (stars) at three arrays.
3. BISL
The BISL technique (Modrak et al., 2010) uses a statistical approach for infrasound location that can appropriately account for both model and measurement uncertainties inherent to infrasound. Phase identification is replaced by the use of a Bayesian prior on group velocity, with both arrival times and backazimuths contributing to the estimation of a location polygon for a specified confidence level.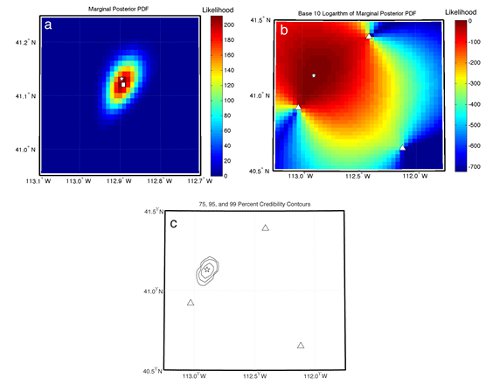
Location: An illustration of the application of BISL to a rocket motor detonation conducted at the Utah Test and Training Range and recorded by three arrays. The location polygons are calculated by taking slices through the posterior PDF (shown as a color plot).
References
Arrowsmith, S.J., Whitaker, R.W., Katz, C. & Hayward, C., 2009. The F-detector Revisited: An Improved Strategy for Signal Detection at Seismic and Infrasound Arrays, Bull. Seism. Soc. Am., 99, 449-453.
Arrowsmith, S.J., Whitaker, R.W., Taylor, S.R., Burlacu, R., Stump, B., Hedlin, M.A.H., Randall, G., Hayward, C. & ReVelle, D., 2008. Regional monitoring of infrasound events using multiple arrays: application to Utah and Washington State, Geophys. J. Int., 175, 291-300.
Drob, D.P., Garces, M., Hedlin, M.A.H. & Brachet, N., 2010. The Temporal Morphology of Infrasound Propagation, Pure appl. geophys.
Garces, M., Hansen, R.A. & Lindquist, K.G., 1998. Traveltimes for infrasonic waves propagating in a stratified atmosphere, Geophys. J. Int., 135, 255-263.
Modrak, R.T., Arrowsmith, S.J. & Anderson, D.N., 2010. A Bayesian framework for infrasound location, Geophys. J. Int., 181, 399-405.
